Advertisers’ businesses boom yearly on Black Friday as they promote their annual sales. Last year, Black Friday saw another big boom — cookie stuffing — marking a sharp increase in fraudulent ad impressions.
Confiant found a cookie-stuffing campaign running across multiple programmatic ad platforms around Black Friday. What did that teach us? Bad actors will use any tactic or occasion to exploit the supply chain.
While ad fraud is not the core focus of Confiant’s business, they work to weed out threat actors who use the programmatic process and ad networks for malicious purposes.
In this case, the bad actor was DatalyMedia, the mastermind behind the campaign.
What is Cookie Stuffing?
Cookie stuffing is ad fraud where a malicious campaign triggers arbitrary numbers of invalid ad conversions by generating fake clicks. It is a source of invalid traffic (IVT), which makes it a form of ad fraud.
Cookie stuffing targets several types of campaigns, including cost-per-click (CPC) ad campaigns, various types of cost-per-lead (CPL), and cost-per-action (CPA) campaigns. Malicious actors typically generate fake clicks by loading click URLs in hidden iframes inside ads as they render.
Don’t expect this malicious practice to die down anytime soon. According to the World Federation of Advertisers (WFA), “ad fraud is likely to exceed $50 billion globally by 2025 on current trends, second only to the drug trade as a source of income for organized crime.”
Both publishers and advertisers should worry about this practice as it affects them both. For publishers, their web page is under attack because cookie stuffing causes page latency. This derives from a massive network overload when the advertising landing pages load in hidden iframes. For advertisers, cookie stuffing distorts targeted data and degrades campaign effectiveness.
In addition, for publishers and advertisers, cookie stuffing creates liabilities for violating privacy compliance regulations and steals money from the ad tech ecosystem.
DatalyMedia’s Strategy
According to the data, DatalyMedia has executed its cookie stuffing schemes since at least 2015. Over time, the infrastructure and techniques DatalyMedia uses for the affiliate marketing fraud scheme have barely changed.
DatalyMedia was caught implementing these tactics to maintain its presence in the ad tech ecosystem by:
- Creating over 100 ad serving domains.
- Partnering with ad platforms. DatalyMedia was active on at least four different advertising DSPs in 2022.
- Approaching ad security vendors about the status of their domains, claiming legitimate needs.
- Cloaking
- They used this tactic to circumvent detection.
- The script that DatalyMedia executes has a cloaking component that loads one or multiple hidden iframes.
- If the cloaking test fails, the bad actors replace the iframe with an empty image.
- If the cloaking test succeeds, the iframe URL redirects to a secondary domain with similar cloaking.
The Ad Tech Cartel: Laundering Via Network of Fake Sites
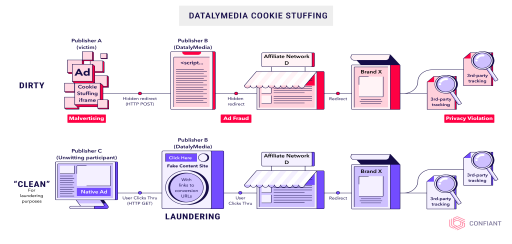
As one of the biggest crime syndicates in the ad tech ecosystem, DatalyMedia and other malicious actors utilized an illegal tactic that kept criminal empires afloat for centuries –– laundering. However, they laundered user data instead of money.
Similar to money laundering, DatalyMedia created two traffic paths, a dirty path that commits fraud and a clean one with legitimate traffic that hides the malicious traffic.
DatalyMedia served programmatic ads on Publisher A’s website in the dirty path, as indicated in the graphic. These ads are cloaked in an invisible iframe to hide the cookie stuffing scheme.
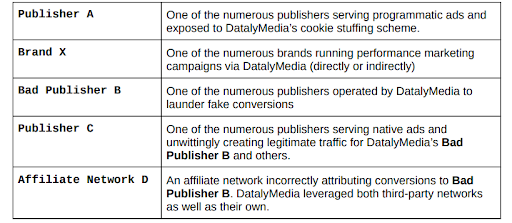
The Affected Players (Both Directly and Indirectly)
As the graphic below highlights, many aspects of the supply chain are affected by cookie fishing. As highlighted in this graphic, the amount of revenue lost serves as a warning for how diligent publishers and advertisers must be to protect themselves from ad fraud.
The next steps:
- The scheme uses an intermediary website (Bad Publisher B), making the conversions look legitimate to the defrauded affiliate networks and brands.
- The “dirty” path uses a POST HTTP request to Bad Publisher B, while the “clean” path uses a GET request.
- The “clean” path uses native ad networks to create traffic in the style of ad-driven content websites, but the real purpose is to create an audience to support the conversions driven by the “dirty” path.
- Traffic generated from the “dirty” path is indistinguishable from the “clean” path traffic.
Final Results
DatalyMedia’s cookie fishing scheme was quite successful. It generated a significant amount of revenue from ad fraud, but their schemes are no longer a secret due to the work of companies like Confiant.
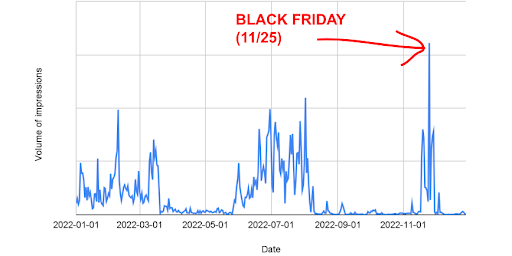
The study estimated that DatalyMedia served approximately 125 million display ad impressions in 2022.
DatalyMedia has had three major periods of seasonal activity over 2022: Winter, Summer, and Fall, and an all-time peak on Black Friday – November 25, with a volume of over 9x their daily 2022 average.
The lack of industry focus on this issue has allowed these fraudsters to thrive,” says Jerome Dangu, CTO & Co-Founder at Confiant. “specifically in the case of DatalyMedia for a mind-blowing eight years.”
Publishers and advertisers, this is your call to action to keep your eyes open for malicious actors. The supply chain is open season for ad fraud schemes, and neither you nor the consumer is immune to their attacks. Lurking under your landing pages and ads are schemers itching at the thought of stealing your revenue.
Read Confiant’s article here: https://blog.confiant.com/malvertiser-makes-the-big-bucks-on-black-friday-637922cd5865