ScamClub, a sophisticated cybercrime syndicate, exploits VAST tags with obfuscated malicious scripts to orchestrate large-scale fraudulent redirects through video ad units. How can you combat them?
Towards the end of last year, my company began to notice an uptick in malicious redirects stemming from video ad units—a first for the digital media ecosystem. Specifically, scammers have begun injecting malicious redirects through VAST tags that redirect users to a fraudulent website, regardless of whether the ad was played or for how long a user watched it.
The redirects started slowly as fraudsters were testing the strategy. In January, however, the number of such attacks exploded. It is the first time we’ve seen such large-scale fraud in video ad formats, which have traditionally been considered safe. In fact, publishers have assumed that the high cost of video inventory was enough of an impediment for fraudsters that they didn’t need to deploy malware detection and mitigation tools to the channel. This assumption of safety was the opening scammers needed to exploit VAST and VPAID ad units.
Our research shows that nearly a dozen major SSPs and DSPs across multiple regions have been affected by these attacks, although mobile devices in the US were the worst hit, accounting for 60% of the attacks.
So, who is behind the scam, how does it work, and, most importantly, what can we do about it?
ScamClub’s Sophisticated Attacks
These scams are the work of ScamClub, a persistent and well-organized crime ring group that has been plying malvertising schemes since 2018. ScamClub uses sophisticated techniques, such as Obfuscation and real-time bidding integration, to push malicious codes to users.
In this scenario, ScamClub actors act as a go-between, selling redirected traffic to other scammers who then trick users into downloading fake antivirus software or purchasing fake gift cards.
How it Works
This is an incredibly sophisticated attack with many mechanisms to prevent security vendors from detecting and reverse engineering them so they know how to block the scam.
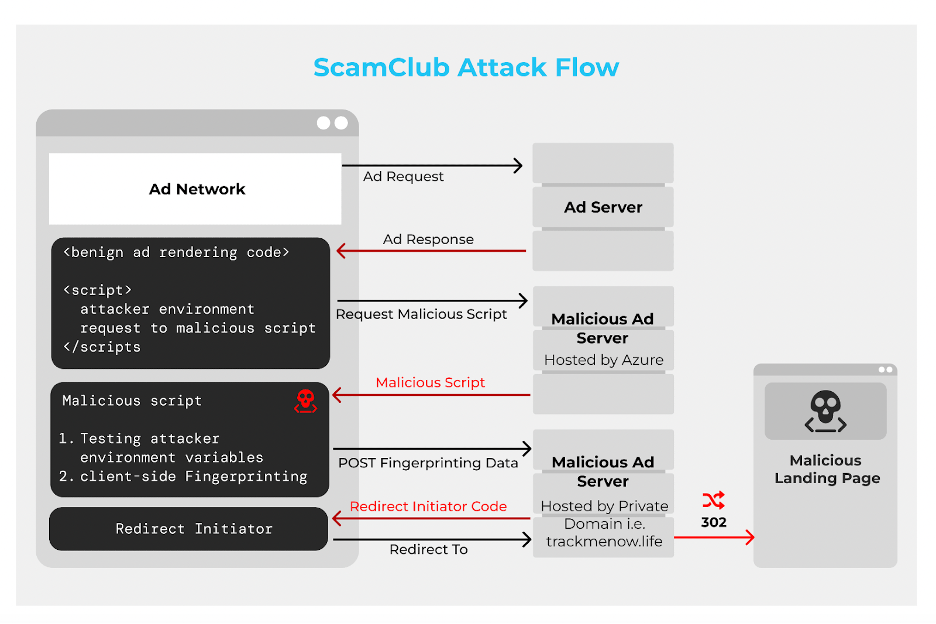
Step: 1: Creating the Malicious Script. The first thing ScamClub did was inject malicious code hidden in the “MediaFile” element of the VAST tag—the same element that calls the ad’s video file. This malicious code collects fingerprinting data about the client to detect clients of a security vendor (if security is detected, the attack isn’t deployed). At this stage, they store the collected data in an environment external to the script.
Step 2: Executing the Malicious Obfuscated Script. This script, which is deliberately scrambled or obfuscated, then probes the client device for information, such as its settings and installed software, looking for suitable targets.
Step 3: Server-Side Fingerprinting. Once the script finishes fingerprinting the client, it proceeds to the server-side fingerprinting phase. Basically, it makes a request to a malicious ad server hosted on a private domain to which it passes additional information about the users’ devices, client applications, and web pages they’re on. This triggers a series of high-level, server-side fingerprinting tests in order to reassure the attackers that their scam will not be exposed to security vendors.
Step 4: Redirect Code. Once the information from the client is sent and checked by the hidden server, the POST request’s reply or response includes instructions that tell the user’s device to go to a new website. This redirect code includes several different methods to initiate the forced redirect. This diversified attack strategy increases the chances of successful redirects, making it harder for security vendors to detect and identify the attack.
Step 5: Redirect Domain Chain. The domain obtained from the redirect code initiates a redirect chain, taking the user to a fraudulent website. This is the final step; they’ve delivered traffic to their clients, who somehow attempt to defraud the user.
In the most recent variant of the ScamClub scam, the attacker moved the malicious script’s hosting server to their own domain instead of Azure.
For a more detailed explanation of this attack, including fingerprinting information inside the attacker environment variable, the fingerprint functions used in the script, and other technical details and sample code, please see Decoding ScamClub’s Malicious VAST Attack.
Protecting Your Inventory
The best way for a publisher is to ensure a real-time protection service (if they don’t already have one) that covers their video demand channels and video players.
Additionally, platforms should consider applying higher scanning rates to their video demand because it is not as safe as they used to think.