Video advertising, once a safe haven in the digital space, is now under siege by malvertising attacks, demanding immediate action from publishers, SSPs, and video platforms to secure their technology stacks.
Video advertising has always been a bright spot for the industry: effective, profitable, and malware-free. Because it’s threat-free, AdOps teams don’t need to spend a lot of time scanning for scams. Sadly, that is changing rapidly.
Earlier this year, I wrote about ScamClub’s breach into the video channel, successfully injecting malicious redirects through VAST and VPAID tags in Q4 2023. Since then, video malvertising attacks have proliferated and show little sign of abating anytime soon. Worse, other scammers have no doubt noted the success of ScamClub’s assault on video ads. In the months ahead, we should expect a surge in automatic and malicious redirects, and everyone — publishers, SSPs, and video platforms — should begin hardening their video tech stack immediately.
How Video Automatic Redirects Work
In case you missed the first article, here’s a rundown of the ScamClub scheme, the first industry-wide attack against video ads. GeoEdge discovered the scheme injected malicious redirects through VAST tags, sending users to a malicious website regardless of whether they played the ad or how long they watched it.
Essentially, the scammers run fingerprinting tests on both the client and the server sides, looking for malware detection systems. Once the information from the client is sent and checked by the malicious server, the POST request’s reply or response includes instructions that tell the user’s device to navigate to a new website. This redirect code includes several different methods to initiate the forced redirect. This diversified attack strategy increases the chances of successful redirects, making it harder for security vendors to detect and identify the attack.
Bad Actors Have Breached Video Advertising
For a long time, video has been considered the safest channel in digital advertising. The high inventory cost has deterred scammers from attacking the channel, concentrating on the abundance of low-cost and vulnerable display ad units. As a result, many publishers, SSPs, and even video platforms haven’t screened for malware even as they actively screen for it in their web and mobile inventory.
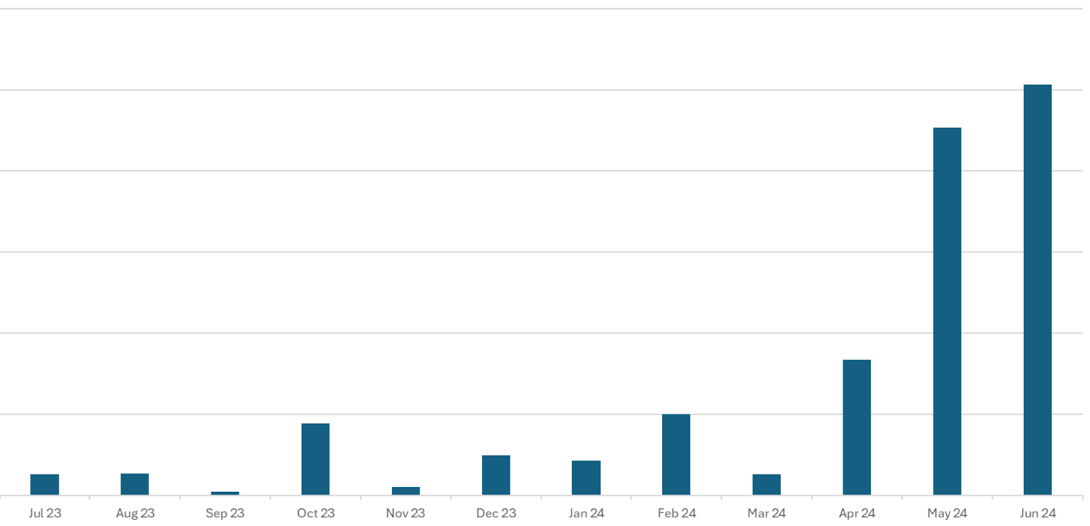
But we need to understand that scammers have breached the video world. GeoEdge’s security research first exposed the video malware epidemic in July 2023, but as you can see in the chart below, the number of instances has escalated dramatically.
We’ve seen dozens of SSPs—all the major industry players—affected by the ScamClub malicious VAST and VPAID attacks. The same goes for video platforms, which scams have infected in equal measure. Any publisher that relies on an SSP or video platform to fill video inventory is likely exposed.
In fact, AdOps teams are now receiving complaints from publishers, who are receiving complaints from their users and editorial team about sketchy ads that pop up on landing pages that look like system messages prompting users to download fake software updates or fake antivirus software that records and transmits their bank information or credentials to the scammer’s servers.
Even though we already see hockey stick growth in the ScamClub version of the attack, we are at the beginning of the growth trajectory. For this reason, we should assume that automatic redirects in video will dramatically increase over the next 12 months.
Time to Harden the End-to-End Video Tech Stack
This means it’s time to harden the video tech stack. Publishers must recognize the importance of monitoring and safeguarding their video technology infrastructure, as it’s no longer secure. This shift in mindset is crucial.
SSPs need to begin to reassess their video demand, with an understanding that they can no longer assume it’s safe. They must acknowledge the presence of malvertising in the channel, which many expect to increase significantly.
Additionally, the entire video platform segment, which supports video players and previously remained unscathed, now faces new threats. These platforms must start monitoring and addressing security issues at their own level.
This, of course, brings up the question of CTV. Is that channel safe? It’s unlikely that consumers will click on ads, visit landing pages, and fill out forms from their smart TVs. However, as QR codes become common in CTV advertising, they will introduce new risks, as fraudsters will have the opportunity to redirect the user who scans that code via a mobile device.
A New Approach Required
Because of the multiple mechanisms that block attacks from security vendors, new approaches are needed. In our experience, it’s not enough to monitor the video ad units themselves but the entire page itself. By monitoring the entire page, security teams can identify, analyze, and classify copycat and emerging variants of redirect scams immediately and proactively block them every time they appear.
A Call to Action
Video is no longer a safe haven; we need to pay attention to it. The channel has been breached, and fraudsters are rushing in. However, we are by no means defenseless. To combat this rising threat, we must embark on a new era of cooperation across the entire industry. By working together, we can identify and mitigate video threats more effectively and share our learnings to strengthen our collective defenses.